The last couple of days I've been looking into WiFi-Security. It came into my perspective by looking at Spacehuhns WiFi Deauther. I already knew a little bit about WiFi-Security before, and heard that WiFi devices send out Probe Requests. My first intention was to build a little Device Monitor that counts how many devices are currently sending WiFi packages in my vicinity. Like this PAX-Counter:
Updates
Update 05.08.2020: As it turns out Apple is listening to it's users :) - with:
iOS > 14 there will be proper MAC Address randomization for WiFi's. You can even control how your iPhone will behave for that particular WiFi.
For example if you're at home you can connect with your real MAC-Address. That allows you to setup a Raspberry Pi which is looking for a connection of that particular MAC, and then you can turn lights on etc. ;) I really like it that Apple leaves that possibility for us. Apple on this:
To reduce this privacy risk, iOS 14, iPadOS 14, and watchOS 7 include a feature that periodically changes the MAC address your device uses with each Wi-Fi network. This randomized MAC address is your device's private Wi-Fi address for that network—until the next time it joins with a different address.
You can read more on this here: https://support.apple.com/en-us/HT211227
I don't know what Android is doing on this topic... If you know something please write it in the comments below :)
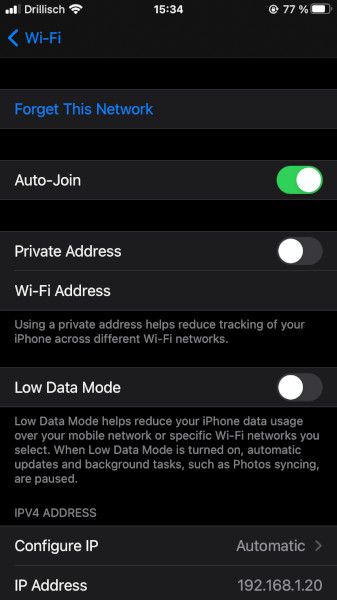
You can disable the private mac address here:
- Go to Settings --> Wi-Fi --> Press on the little blue (i) at the listed WiFi --> Disable "Private Address".
Update 21.Juli 2020: I was looking into BLE with an ESP32 and looking for Corona-Contact-Protocol Packages, as it turns out on iOS 15 Apple is randomizing the Bluetooth MAC Address. That's cool :) I wrote a blog about it: Link
Probe Requests
So I've setup my network card in monitor mode and started airodump-ng. It also shows all the devices which are not connected to an WiFi access point. What I observed were Probe Requests from devices in my neighborhood. But also Probe Requests, which send out my SSID from my own WiFi. They came from my iPhone, and they looked like this:
12:34:56:78:9A:BC E4:E4:AB:AB:CD:EF -4 0e-24 0 24 myWifi
Obviously I've changed the MAC so on the left 123... is my Access Point and E4:E4:AB:AB:CD:EF is my iPhone. First I thought, well that's no MAC address randomization. And actually in this case, there is no MAC address randomization.

When you're using iOS. the MAC randomization is only active when your phone is not associated with an Access Point. (02/2019)
So I deactivated my Access Point and looked at the probe requests from my iPhone and from my iPad:
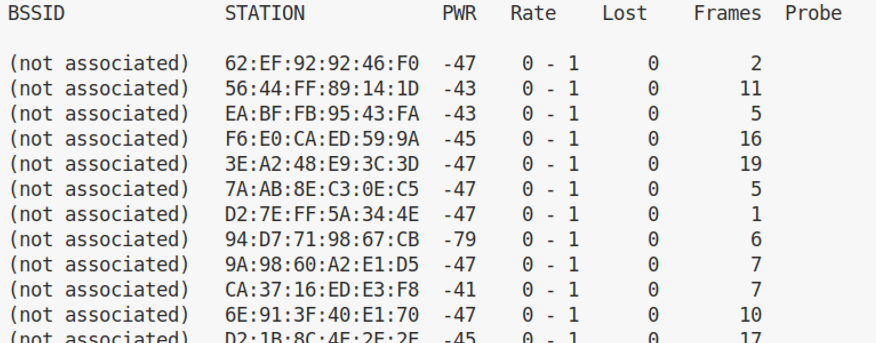
Apple is using a locally administered address here. You can distinguish a locally administered address when the second-least-significant bit of the first octet is 0. If it's 1 it's a universal administered address.
for example:
62:EF:92:92:46:F0
//so in binary:
0110 0010 : 1110 1111 : ...
^
|------ this one
So basically if you encounter MAC addresses which begin like:
0xX2 --> 0b0010
0xX6 --> 0b0110
0xXA --> 0b1010
0xXB --> 0b1011
0xXC --> 0b1100
0xXD --> 0b1101
0xXE --> 0b1110
0xXF --> 0b1111
than the MAC address is locally administered. As it turns out you also could use an randomized MAC address for the WiFi when you're connected to an AP. This is done for example by Microsoft in Windows 10. They do this with a SHA-256 which looks like this:
addr = SHA-256(SSID, macaddr, connId, secret) (Source)
In my opinion this is the best way to go.
Good things
The good thing is, that the iPhone doesn't send out all the known SSIDs. And it does MAC address randomization when probing for WiFi's. (unassociated)
Bad things
When your phone sends out a probe requests with an SSID, you could not only identify the user, but also locate him where he lives. Especially if he was really creative with his WiFi-SSID. You could do this with a database query at wigle.org. On wigle.org users (and organizations?!) upload MAC address surveys from their laptop or phone. Just search for the 'unique' WiFi address. And even on Android phones, which do MAC randomization the phones send out the SSIDs. Someone could just create an fake AP with one of those SSIDs and the device will automatically connect to it. This even works with RADIUS. So basically the phone is basically screaming out loud the SSIDs it wants to connect to, then someone sees these SSIDs, creates an fake AP and the phone will try to connect to it. There is no authentication if the WiFi is an unencrypted one, like the ones you find at coffee shops. Your phone will not know that there is an Fake-AP.
Prevent tracking
So how to prevent tracking? Flight Mode (also disable WiFi and Bluetooth) and turning off your device would work ;).
But you could also make it a little bit harder. For example by naming the SSID from your WiFi at home to some really common WiFi name. There is actually a gist on GitHub with the most common 5000 WiFi names. Choose one of these.
Delete WiFi's you don't need from your WiFi-List. Especially if it was a unsecured WiFi. To summarize:
- Delete unused WiFi on your phone
- Use an common SSID for your WiFi at home.
- Turn WiFi off whenever you don't need it.
- Never connect to WiFi that are not encrypted or where an attacker could know the WiFi-Password
Off course you will be track-able by your mobile provider. But not by some company which tracks users not only in certain stores but over many stores you visit.
Conclusion
So the MAC randomization is good, but it could be better. If your iPhone already knows a WiFi, it will connect to it. In my case it's always the University WiFi. Some of you guys know eduroam? It's practically everywhere. And now I know why so many fast food restaurants, Swedish furniture stores, coffee shops etc. offer free WiFi. Your iPhone will connect to it, and the owner will know when and how often you're visiting his store. If this would take place completely anonymized I wouldn't complain, but who knows what they're logging.


If you press this Button it will Load Disqus-Comments. More on Disqus Privacy: Link